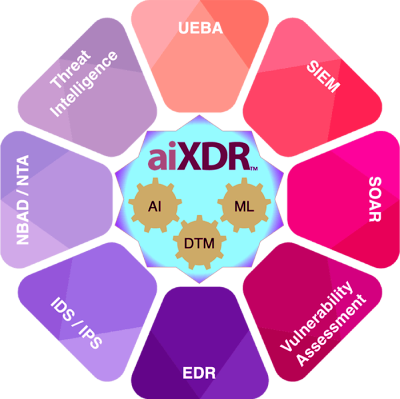
aiXDR protects your borders – remote office, cloud, office, or in transit with the help of razor-sharp analytics, led by Artificial Intelligence and Machine Learning.
Any flaw might cause a loop hole for the attackers in this evolving context of remote workplaces and sophisticated attacks.
- Malware downloaded through a malicious website or a spam email.
- Brute-force attacks on endpoint users’ credentials
- Unmonitored use of VPN to access torrent files
- Business and privacy protected information leakage by employee
- Use of public Wi-Fi for sensitive data business applications
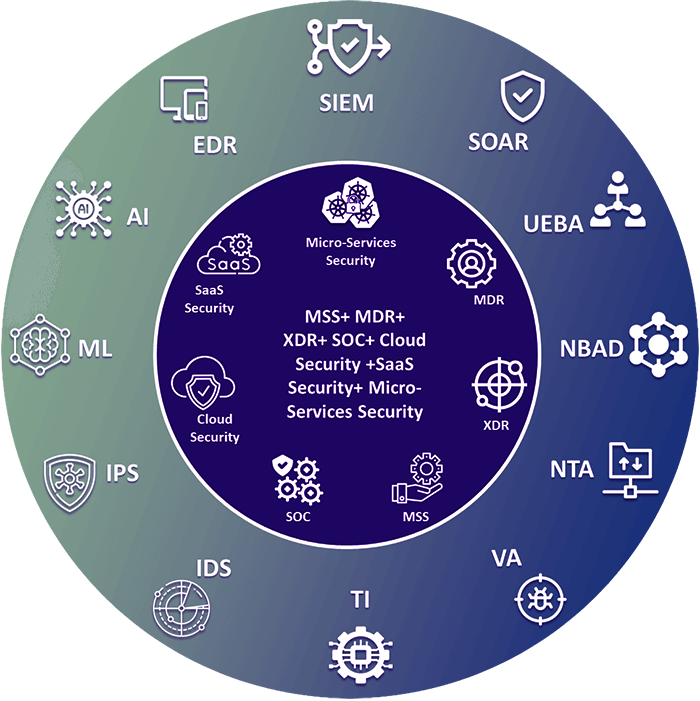
Purely depending on layered protections such as EDR, IDS/IPS, SIEM, SOAR, or Network Security will not provide effective security for your company’s vital assets. aiXDR is a fusion of all of these defensive layers, developed organically with real-time analytics, defense in-depth supervision, and dynamically adaptable threat models led by Artificial Intelligence. It eliminates the grey and white spaces in cyber security, making it a true “One Stop Shop” for multi-layered protection against threats, attacks, compromises, and exploits.
Comprehensive security for your digital assets
Rich and pertinent evidence derived from various sources
Powerful AI, ML and DTM to preempt incidents