7 Pillars of Zero Trust Security

Resources
An organization should treat all of their data, computing services, and devices as resources that need to be protected.

Communication
All communication, both from within and outside the network, must be treated the same and protected in the most secure method available.

Per-Session Access
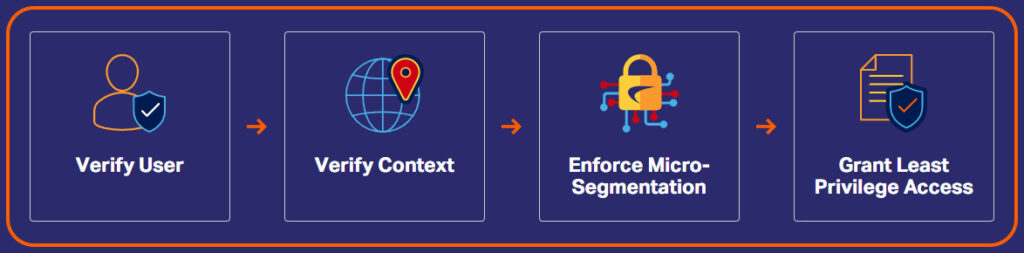
Each connection to a critical resource or an organization should be established on a per-session basis only.

Dynamic Policy
Access to an organization’s resources should be granted according to the organization’s policy rules and the principle of dynamic least privilege.

Monitoring
To ensure proper data protection and security of corporate resources, organizations should monitor those resources and all actions taken with them.

Continuous Improvement
An organization should gather information about the current state of network assets, infrastructure, and connections to improve the security posture of the network.

Authentication and Authorization
Before granting access to any corporate resource, an organization should enforce dynamic authentication and authorization.